This post contains links to the Keystroke and Mouse Recorder demo that I created using PHP, Javascript, JSON, AJAX to show how easy it is to “screen record” your mouse movements and keyboard strokes (including password and credit card info) on the web.
The Web Page Keystroke and Mouse Recording Demo
I think it’s best for you to actually see the demo so you can appreciate how easy this is.
There are two parts to this demo. One is the “recorder” which is where you will move your mouse around, type username and passwords in, etc. The other is the “player” that will show you in real-time all the activity from the “recorder”.
HOLD THE SHIFT KEY ON YOUR KEYBOARD WHILE CLICKING ON THE TWO LINKS BELOW TO LAUNCH INTO A NEW WINDOW!
Launch the Keystroke and Mouse RECORDER by Clicking Here (this screen will be “recorded”; pink bar across top of window)
Launch the PLAYER (Spying Window) by Clicking Here; this will show all the keystrokes and movements from the other window (this screen will show you all activity from the Recorder window; blue bar across top of window)
I have only tested this demo on a computer (not a phone or tablet).
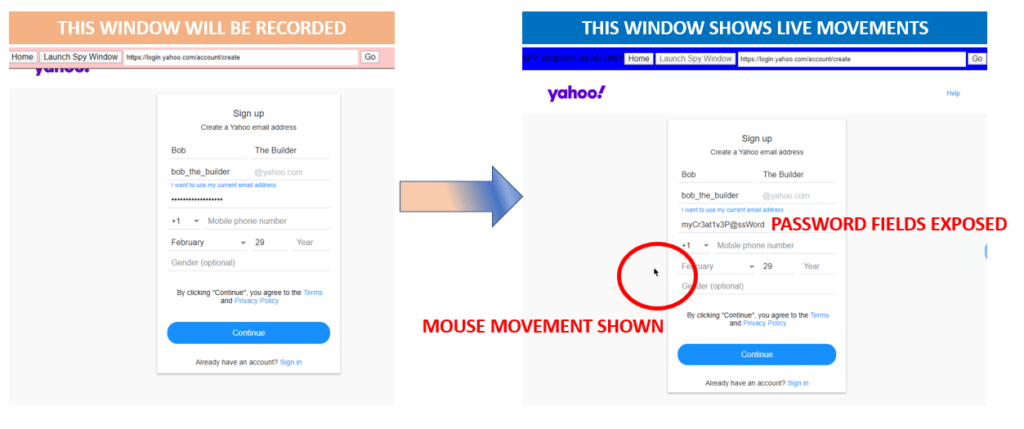
It is best if you move these two windows to be side-by-side (have them in their own window) so that you can see everything update real-time. If you have two monitors, drag each window onto its own monitor.
Use the pink bar’d window to do all your typing and mouse movements and the blue bar’d window to watch all the activity.
The demo launches you to the actual Create an Account Page for Yahoo but you can go to any web page you like. Google.com? Facebook.com? You name it. I tried to make the player follow your movement around the web from the recorder as you click on links but sometimes websites will directly link to their own site and break the proxy link.
The scary thing is that the “Player” could really be anywhere in the world and has no requirement to be on the same computer that the “Recorder” is on. So this means someone else could be watching all your movements.
Why did I do this?
I had a random thought the other day on how technically easy it is for hackers and phishers to record your keystrokes and mouse movements as you are browsing the web, without you even hitting submit on a website.. and I thought why not create a quick demo to illustrate this.
Often times people think that if they don’t hit submit on a website, then they aren’t at risk in sending data to the wrong party. This is simply NOT true. If by instinct you start to type in your username and password on a phishing attack, but then quickly realize it’s a bogus website, it likely is too late. Or even worse, if you have auto-complete on and/or somehow they have spoof’d the targeted domain, your data could immediately be sent to hackers.. even if you closed the browser a split second later.
Due to technology that has been around forever, it is easy to secretly send data in the background which could include your mouse movements, every key you type or delete, and more. And often times, major tech companies are using this very technology to send information stealthily in the background for analytics reasons.
How did I do this?
I started out by creating a simple PHP script that accepts JSON data from a client (you), sends this data back out to anybody that asks for it (however, I decided to limit it to the same web session to prevent abuse). Then I created the some javascript that will listen for mouse movements, dynamically scrape all input fields on the page, change all password fields to viewable text fields on the Player, and then transform that into JSON and send it to my PHP script. Finally, I decided to integrate this concept with a PHP Proxy Server script so that I could record any web page’s movement. I felt like doing this would make it more realistic for you instead of showing you some boring form I created.
This is just a demo
This is a demo so it’s not perfect and not all websites will load perfectly. Although I tried to accommodate the programming styles (being flexible in the grabbing of ID’s or Names’s for input elements) there could be other issues that prevent the proxy script from working correctly. Also, because this is a proxy script, if you visit many sites then you could overload your browser with tons of cookies for my site that will eventually cause an HTTP error complaining about the size of the header your browser is sending to my site. If you see this, simply clear your cookies for my site and that should resolve the issue.
This exposes a few possibilities
A few things come to mind as possible exploits and vulnerabilities this demo implies.
- By compromising a commercial website with very little javascript injected into the website’s HTML files, and a 10-15 line PHP (or any language) script, one could easily be grabbing usernames, passwords, and other PI data without ever touching a database or application code. It would be very difficult to trace.
- The data could be cached locally, encrypted, and sent out periodically to a third party server to avoid constant contact.
- This third party server could be running some common port services that are not accessed other than through a standard port 80 that allows for secretly tunneling the packets by the hacker. The hacker could respond with generic looking blog pages on cats when the IT administrator does discover something going to this third party server. Upon seeing blog activity on port 80, this could alert the hacker that someone is onto them.
- Developers could be putting a lot of security in protecting the data from its users but it’s all useless protection with an attack like this since this script is grabbing it straight from the user’s web browser and sending it to the hackers own script. This means that additional precautions must be made to ensure that companies don’t inadvertently host malicious files.
- It is very easy for someone to come up with a clever URL that looks similar to the one you want to visit (e.g. your bank, social media) and have it simply be a proxy site that is scraping your inputs and mouse movements. This would be very similar to the demo I just showed you but without the pink and blue banner on the top alerting you to the motive.
- Auto complete could be exploited to easily grab information that gets filled out when the user goes to the site. This could involve input fields that are “below the fold” that include lots of personal information. And if this script was put onto a legitimate website, the saved username/passwords get immediately inputted by your browser and are easy to grab and send to a hacker before you have a chance to erase!
The moral of the story.. always be careful on what you type, even if you don’t hit ‘submit’. And just be aware of what’s possible.
Well, that was fun. Any questions, let me know!
-Ryan

I have been around IT since I was in high school (running a customized BBS, and hacking) and am not the typical person that finds one area of interest at work; I have designed databases, automated IT processes, written code at the driver level and all the way up to the GUI level, ran an international software engineering team, started an e-commerce business that generated over $1M, ran a $5B product marketing team for one of the largest semiconductor players in the world, traveled as a sales engineer for the largest storage OEM in the world, researched and developed strategy for one of the top 5 enterprise storage providers, and traveled around the world helping various companies make investment decisions in startups. I also am extremely passionate about uncovering insights from any data set. I just like to have fun by making a notable difference, influencing others, and to work with smart people.